Blame
| 6e7d20 | Hargata Softworks | 2024-02-16 02:25:37 | 1 | # Authenticating via OpenID Connect |
| 2 | ||||
| a8fb0f | Hargata Softworks | 2025-10-03 22:46:49 | 3 | Configure OIDC for LubeLogger using the [[Server Settings Configurator|Installation/Server Settings]] |
| 6e7d20 | Hargata Softworks | 2024-02-16 02:25:37 | 4 | |
| a8fb0f | Hargata Softworks | 2025-10-03 22:46:49 | 5 | The following sample shows how to set up OIDC with Google as the provider with the LubeLogger instance running on `https://localhost:5000` |
| 6e7d20 | Hargata Softworks | 2024-02-16 02:25:37 | 6 | |
| a8fb0f | Hargata Softworks | 2025-10-03 22:46:49 | 7 | 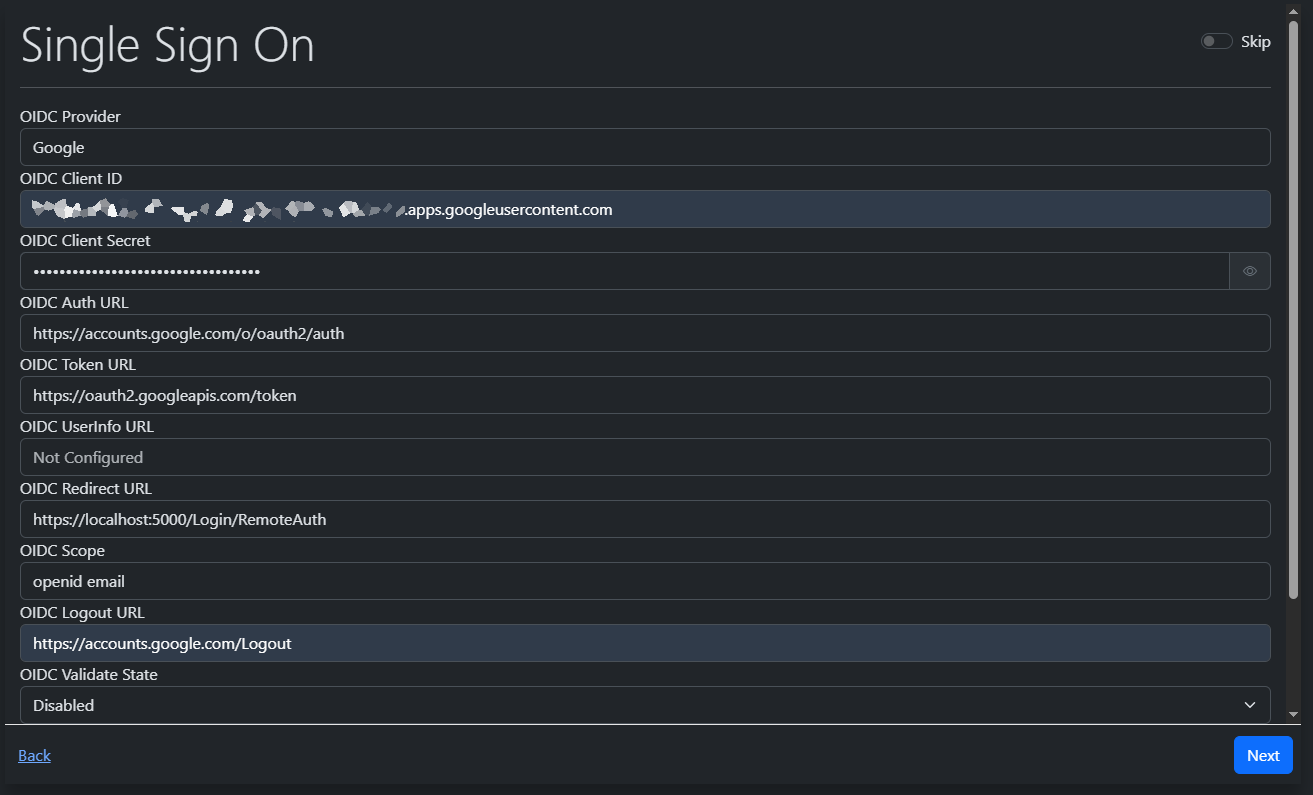 |
| 6e7d20 | Hargata Softworks | 2024-02-16 02:25:37 | 8 | |
| 639e27 | Hargata Softworks | 2024-02-24 16:58:08 | 9 | ## State Validation |
| a8fb0f | Hargata Softworks | 2025-10-03 22:46:49 | 10 | When enabled, LubeLogger will validate the state token echoed back by the OIDC provider and will fail any login attempts where the state token is not identical to what it sent to the provider. Leave this disabled if you wish to have IdP-initiated SSO. |
| 639e27 | Hargata Softworks | 2024-02-24 16:58:08 | 11 | |
| 0449d6 | Hargata Softworks | 2024-08-20 19:58:08 | 12 | ## Proof of KeyCode Exchange(PKCE) |
| a8fb0f | Hargata Softworks | 2025-10-03 22:46:49 | 13 | When enabled, LubeLogger will generate and pass in a SHA-256-hashed challenge code to the OIDC provider. |
| 0449d6 | Hargata Softworks | 2024-08-20 19:58:08 | 14 | |
| 639e27 | Hargata Softworks | 2024-02-24 16:58:08 | 15 | ## Testing |
| 6e7d20 | Hargata Softworks | 2024-02-16 02:25:37 | 16 | Once you have all these environment variables injected correctly, you should see the ability to login via your OIDC provider. Note: Currently LubeLogger only supports one OIDC provider. |
| 5e9566 | Hargata Softworks | 2024-02-16 03:04:40 | 17 | |
| 2b40a9 | DESKTOP-T0O5CDB\DESK-555BD | 2024-09-20 15:19:12 | 18 | 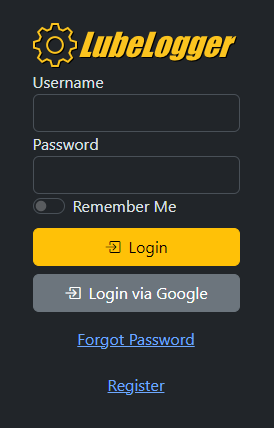 |
| 5e9566 | Hargata Softworks | 2024-02-16 03:04:40 | 19 | |
| 2b40a9 | DESKTOP-T0O5CDB\DESK-555BD | 2024-09-20 15:19:12 | 20 | 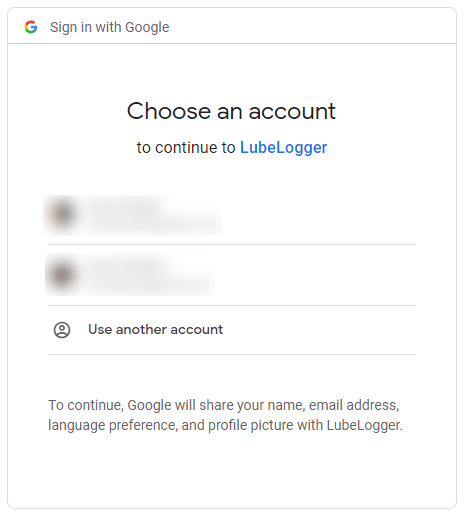 |
| 5e9566 | Hargata Softworks | 2024-02-16 03:04:40 | 21 | |
| d483b9 | Hargata Softworks | 2024-02-17 00:06:23 | 22 | LubeLogger uses the user's email address to authenticate against a registered user, the email address provided by the OIDC provider must match the email address of the user in the system. |
| 5e9566 | Hargata Softworks | 2024-02-16 03:04:40 | 23 | |
| c73afa | Hargata Softworks | 2024-02-17 00:08:13 | 24 | If the user is attempting to login via OIDC but does not have an account with LubeLogger, they will be prompted for a registration token and to set up a username which will then allow them to log in. Note that the registration token is only required for their first time logging in. |
| 12fe29 | Hargata Softworks | 2025-03-31 15:07:07 | 25 | |
| 26 | ### Advanced Troubleshooting | |||
| 27 | ||||
| fb31a1 | Hargata Softworks | 2025-04-02 14:44:20 | 28 | The Remote Auth Debug endpoint allows users to diagnose OIDC-related issues by stepping through it: |
| 12fe29 | Hargata Softworks | 2025-03-31 15:07:07 | 29 | |
| 30 | 1. Set `OpenIDConfig__RedirectURL` to `https://yourlubeloggerdomain/Login/RemoteAuthDebug` | |||
| 31 | 2. Configure your OpenID Provider so that `https://yourlubeloggerdomain/Login/RemoteAuthDebug` is a valid Redirect URL | |||
| 32 | 3. Login using OIDC, instead of being redirected to login, you will be redirected to a page that displays checks and results. | |||
| 33 | ||||
| 27e815 | Hargata Softworks | 2025-03-31 15:09:18 | 34 | Example scenarios(details redacted): |
| 12fe29 | Hargata Softworks | 2025-03-31 15:07:07 | 35 | |
| 36 | All checks passed and a user is identified: | |||
| 37 | ||||
| 38 | 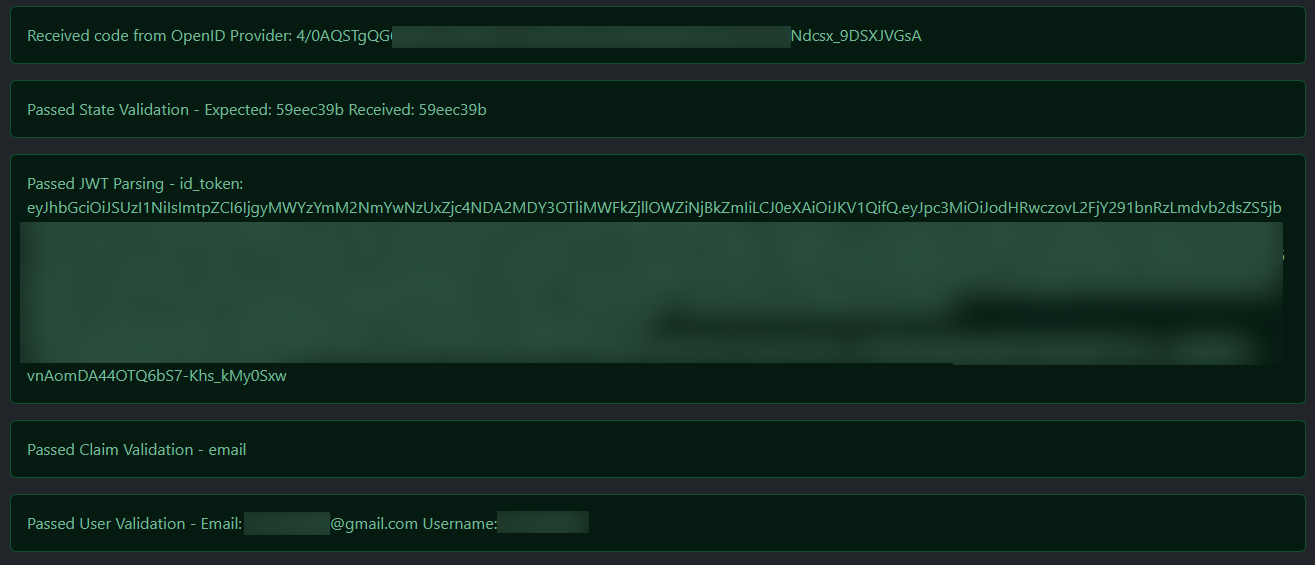 | |||
| 39 | ||||
| 998cc8 | Hargata Softworks | 2025-03-31 15:29:57 | 40 | All checks passed but no user is identified with the email(will be redirected to register under normal circumstances) |
| 12fe29 | Hargata Softworks | 2025-03-31 15:07:07 | 41 | |
| 42 | 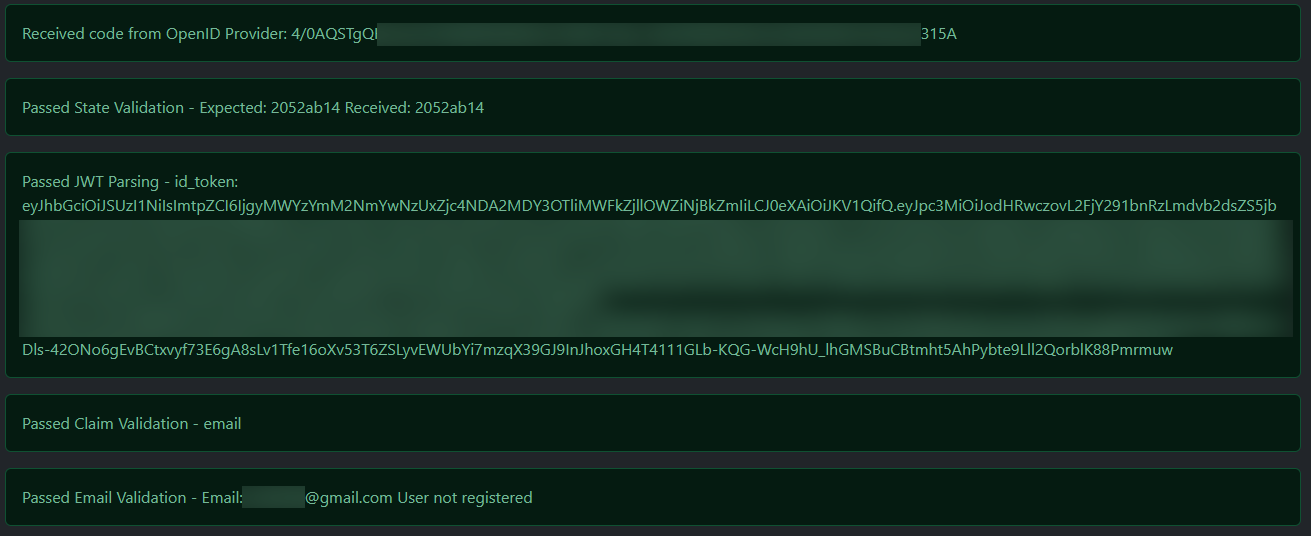 | |||
| 43 | ||||
| 37a95e | Hargata Softworks | 2025-03-31 15:08:29 | 44 | Failed State Validation, Expired OpenID Code and/or OpenID not returning `id_token`: |
| 12fe29 | Hargata Softworks | 2025-03-31 15:07:07 | 45 | |
| 46 | 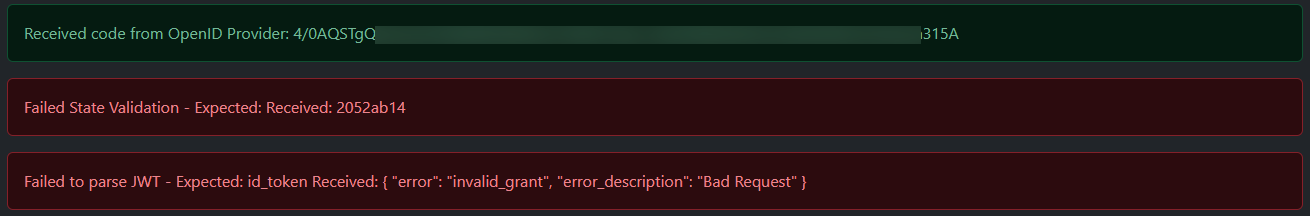 | |||
| 47 | ||||
| 48 | Failed Claim Validation(no email returned from OpenID Provider): | |||
| 49 | ||||
| 50 | 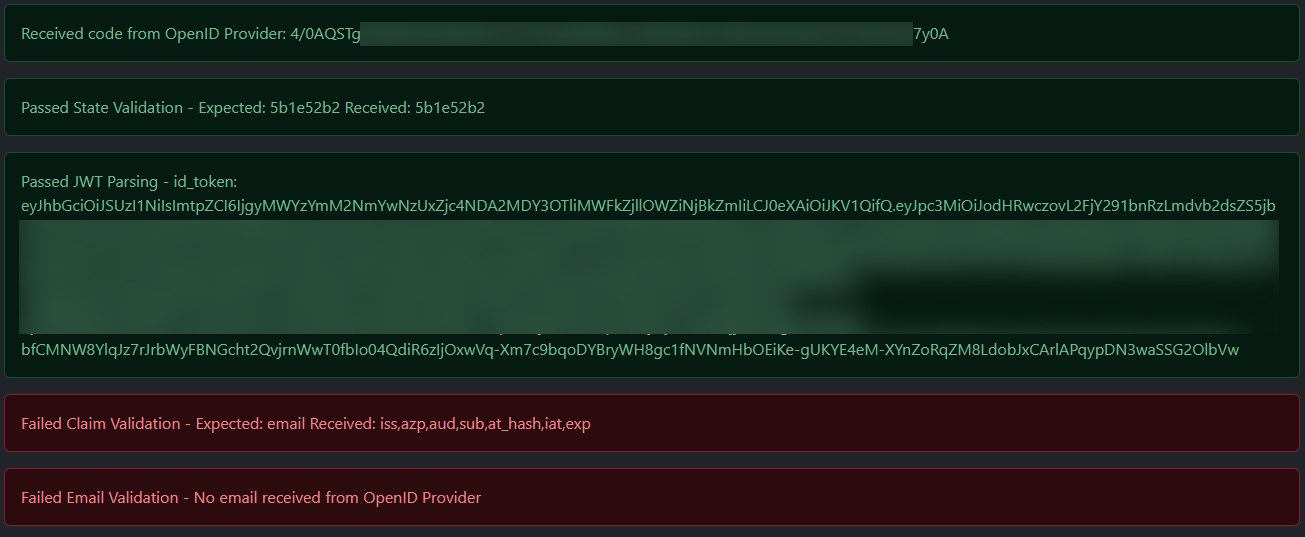 | |||
| 3b61c5 | Hargata Softworks | 2025-04-05 14:46:04 | 51 | |
| 52 | #### Authelia >= v4.39 | |||
| 53 | ||||
| 54 | There are [breaking changes](https://www.authelia.com/integration/openid-connect/openid-connect-1.0-claims/#restore-functionality-prior-to-claims-parameter) for users using Authelia with version >= 4.39 | |||
| 55 | ||||
| f0d944 | Hargata Softworks | 2025-04-29 14:54:17 | 56 | This is because LubeLogger utilizes the legacy method of retrieving the email claim via the id_token, which Authelia has deprecated as of v4.39. |
| 57 | ||||
| 58 | If you're using LubeLogger <= v1.4.6, use the workaround below, otherwise, you can inject your Authelia's userinfo endpoint into the UserInfoURL environment variable, note that `userinfo_signed_response_alg` must be `none` in order for LubeLogger to integrate properly with Authelia | |||
| 3b61c5 | Hargata Softworks | 2025-04-05 14:46:04 | 59 | |
| 60 | Authelia config in identity_providers: | |||
| 61 | ||||
| 62 | ``` | |||
| 63 | identity_providers: | |||
| 64 | oidc: | |||
| 65 | claims_policies: | |||
| 66 | legacy_claims: | |||
| 67 | id_token: ['email', 'email_verified', 'preferred_username', 'name'] | |||
| 68 | ... | |||
| 69 | ``` | |||
| 70 | ||||
| 71 | Authelia config for LubeLogger client: | |||
| 72 | ||||
| 73 | ``` | |||
| 74 | - client_id: lubelogger | |||
| 75 | client_name: "Lube Logger" | |||
| 76 | ... | |||
| 77 | claims_policy: "legacy_claims" | |||
| 78 | ``` |
